Adding Users and Privileges in Linux#
When you first receive a server, it is common to disable root user login and use another regular user. In this case, you need to create a new user.
Adding a User#
Create a new user:
$ useradd boo
Set a password:
$ passwd boo
Privileges#
At this point, the user can already be used normally, but they do not have privileges, so there are many things they cannot do. You can add the user to the sudo group to elevate their privileges using the sudo command.
$ usermod -G sudo boo
Usually, this will add the user successfully. However, some distributions do not have a default sudo group, so you need to add the group first.

$ groupadd sudo
The above image is the visudo configuration file for a Linux distribution with the sudo group.
After manually adding the user group, you also need to modify the sudoers configuration file. There are several ways to do this, depending on the situation:
- Allow members of the
sudogroup to execute any command
$ sudo visudo // or sudo vim /etc/sudoers
// Add the following content
# the 'sudo' group has all the sudo privileges
%sudo ALL=(ALL:ALL) ALL
- Allow the user to execute any command directly
$ sudo visudo
// Add the following content, note: no %
boo ALL=(ALL:ALL) ALL
It is generally recommended to add the user to the sudo group and grant privileges to members of the sudo group, rather than directly elevating privileges for a specific user.
Summary#
View the list of all users:
$ cat /etc/passwd
View all user groups:
$ cat /etc/group
View the groups of the currently logged-in user:
$ groups
View the groups of a specific user:
$ groups username
Add a user:
$ useradd username
Set (reset) a password:
$ passwd username
Add a user group:
$ groupadd group_name
Add a user to a group:
$ usermod -G group_name username
Edit the visudo configuration file:
$ sudo visudo
Disable Root User Login#
1. Change the root user's shell#
The simplest way to disable root user login is to change its shell from /bin/bash or /bin/sh (or any other shell that allows user login) to /sbin/nologin in the /etc/passwd file. You can use any command-line editor to open the file for editing.
> vim /etc/passwd
Change the line:
root:x:0:0:root:/root:/bin/bash
to
root:x:0:0:root:/root:/sbin/nologin
When the root user logs in, they will receive the message "This account is currently not available." This is the default message, but you can change it and set a custom message in the /etc/nologin.txt file.
This method only works for programs that require a shell for user login, such as sudo, ftp, and email clients that access the root account.
2. Disable root login via console devices (TTY)#
The second method uses the PAM module pam_securetty, which only allows root user login on secure TTY devices defined in the /etc/securetty file.
To prevent root login on any device connected to the computer system, clear the file.
> mv /etc/securetty /etc/securetty.orig
> touch /etc/securetty
> chmod 600 /etc/securetty
This method has limitations and only affects login, display managers (such as gdm, kdm, and xdm), and network services on other startup TTYs. Programs like su, sudo, and ssh as well as other related OpenSSH tools can still access the root account.
3. Disable root login via SSH#
The most common way to access a remote server or VPS is through SSH, and you can prevent root user login by editing the /etc/ssh/sshd_config file.
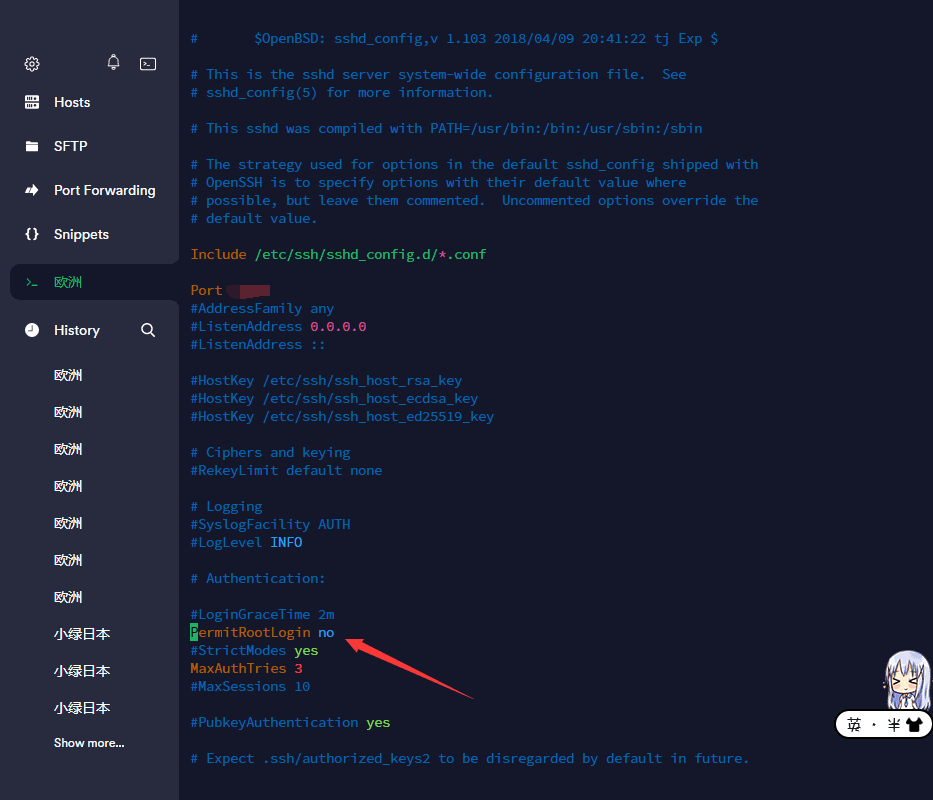
> vim /etc/ssh/sshd_config
Then uncomment PermitRootLogin (if commented) and set its value to no.
After making the changes, save and close the file. Then restart the SSHD service to apply the recent configuration changes.
> systemctl restart sshd
OR
> service sshd restart
This method only affects the OpenSSH toolset and will block programs like ssh, scp, sftp, etc. from accessing the root account.
4. Restrict root access to services through PAM#
Pluggable Authentication Modules (PAM) is a centralized, pluggable, modular, and flexible authentication method on Linux systems. PAM, with the help of the /lib/security/pam_listfile.so module, provides great flexibility in restricting the privileges of specific accounts.
The above module can be used to reference a list of users who are not allowed to log in to certain target services (such as login, ssh, and any PAM-aware programs).
In this case, we want to disable root user access to the system by restricting access to the login and sshd services. First, open and edit the files in the target services in the /etc/pam.d/ directory as shown in the image.
> vim /etc/pam.d/login
OR
sudo vim /etc/pam.d/sshd
Next, add the following configuration in both files.
auth required pam_listfile.so \
onerr=succeed item=user sense=deny file=/etc/ssh/deniedusers
After making the changes, save and close each file. Then create an empty file /etc/ssh/deniedusers. Each line should contain one entry and the file should not be world-readable.
Add the name root to it, then save and close it.
> vim /etc/ssh/deniedusers
Also, set the required permissions for it.
> chmod 600 /etc/ssh/deniedusers
This method only affects programs and services that support PAM. You can block root access to the system through programs like FTP and email clients.
For more information, refer to the relevant manual pages.
$ man pam_securetty
$ man sshd_config
$ man pam